Hex File Generator Tools Particle
The HEX Editor App, which allows you to view and edit raw data, is a fantastic tool for anyone interested in data analysis and editing. Best10Apps.com’s Editor’s Picked is an excellent download, as it is in the Editor’s Picked section. The app is simple to use, and it provides a great way to explore the contents of files.

These files may be in a proprietary object file format specific stock ROMs to the toolchain, but are often standard “open” formats such as ELF. However strictly the meta-data components of an object file are not part of the firmware since they are not loaded on the target. Other significant difference is the stack pointer, on OSs user code will not reserve memory for the stack by itself, it relays on OS for that. When on firmware, you have to do it in user code for the same reason as before, there’s no middle man to manage it for you.
- Or, visit your hardware manufacturer’s support website for more information on firmware updates.
- In response the motor controller increases the torque (orange line) to counteract this disturbance up to a peak of 500 N.cm at which point the motor current limit is reached.
- Actually finding the bootloader binary proved difficult.
- The selection is made by dragging the mouse or holding the Shift key while moving the cursor, just like in a text editor.
There are many types of technology-specific firmware, but all firmware can generally be sorted into three categories based on the level of hardware integration. The EI-ISAC Cybersecurity Spotlight is a practical explanation of a common cybersecurity concept, event, or practice and its application to Elections Infrastructure security. It is intended to provide EI-ISAC members with a working understanding of common technical topics in the cybersecurity industry. If you would like to request a specific term or practice that may be of interest to the elections community, please contact [email protected]. The Original Equipment Manufacturer (OEM) Signer module contains a secure device with a unique set of Manufacturing Public and Private keys. It also contains a Manufacturing Certificate that has a digital signature root of trust which is a critical component in the Chain of Trust.
- The firmware transfer process should take about a minute.
- In a device, a firmware update is used to update the firmware.
- The easiest way to find correct serial port values is to look at other example configurations that use an identical or similar board.
- There are various ways to program the nRF Sniffer firmware.
- Hard drives, video cards, keyboards, and BIOS are a few examples of hardware components that contain a set of instructions permanently carved into them.
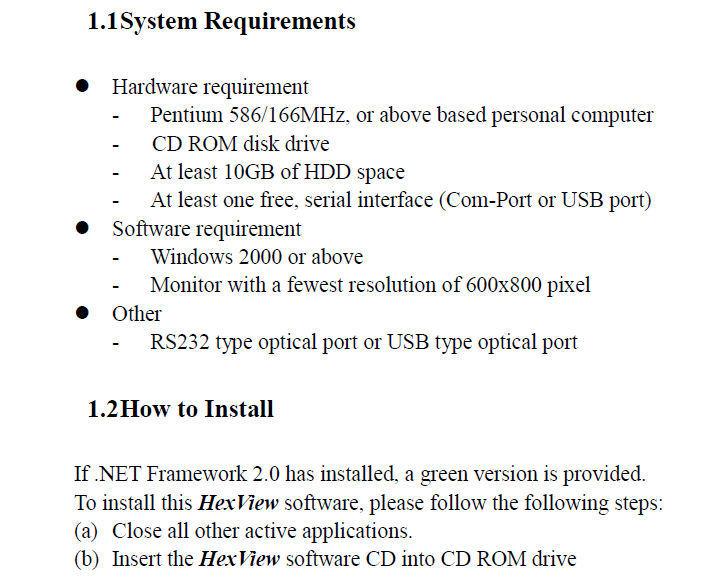
If you modify the .HEX file, it will not get aligned with the checksum. It will cause error during programming, hence not recommended to edit the .HEX file. The result of this operation is a file that will be flashed into (I guess) the flash memory of a MCU such an ARM or a AVR.
